Provides secure remote access
The perimeter expands to remote endpoints, it is imperative to protect the network through proper authentication of workers and third parties. T
Features
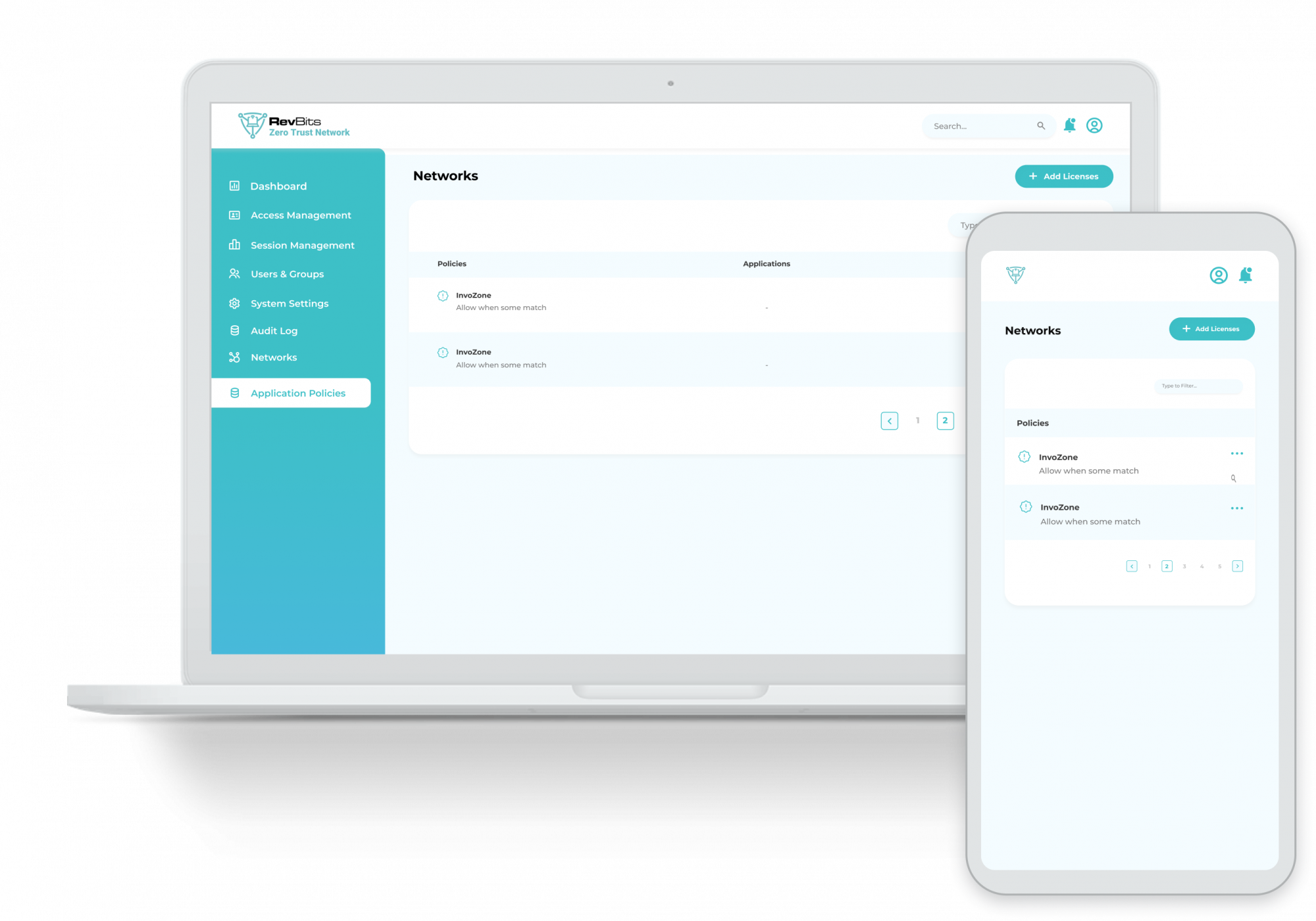
Capabilities – As remote workforces grow and third-party access needs increase, the need for proper network security has far surpassed simple VPN applications. While VPNs provide a level of protection by encrypting incoming traffic, they fall short because they do not provide incoming user authentication—in other words, VPN security stops at the network perimeter. RevBits Zero Trust Network (ZTN) protects the perimeter wherever you are and extends complete security to the network, its assets and applications.
Secure Internet Connectivity - Let RevBits ZTN take care of secure Internet connectivity and authentication for remote users. With the RevBits ZTN secure portal, users will securely connect to network assets over the Internet. Secure connections ensure that network access is controlled and secure.
Fast and secure connections around the world - With over 24 geographically distributed cloud regions, Rev Bits ZTN has proxy servers available for remote network access anywhere in the world.
Access
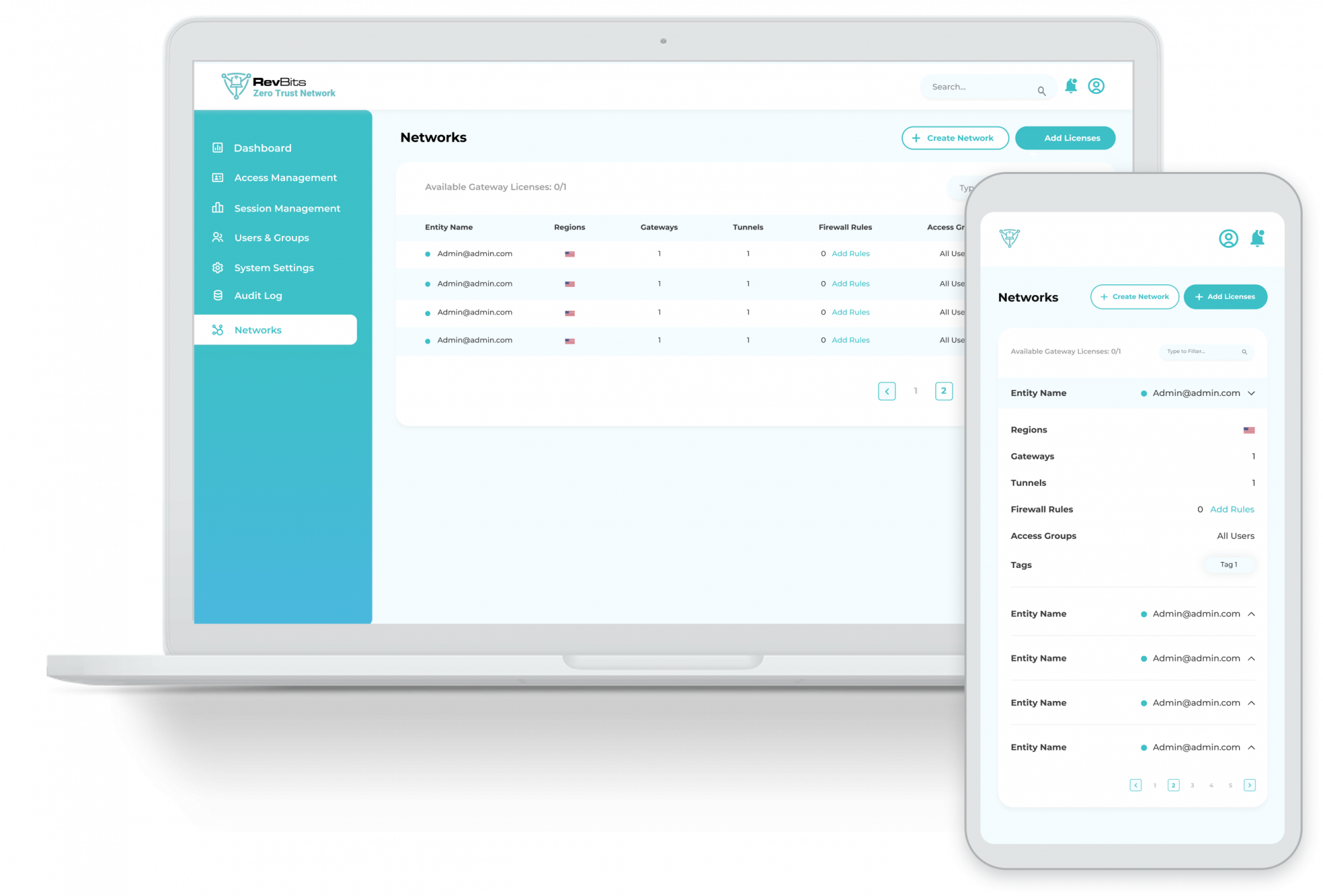
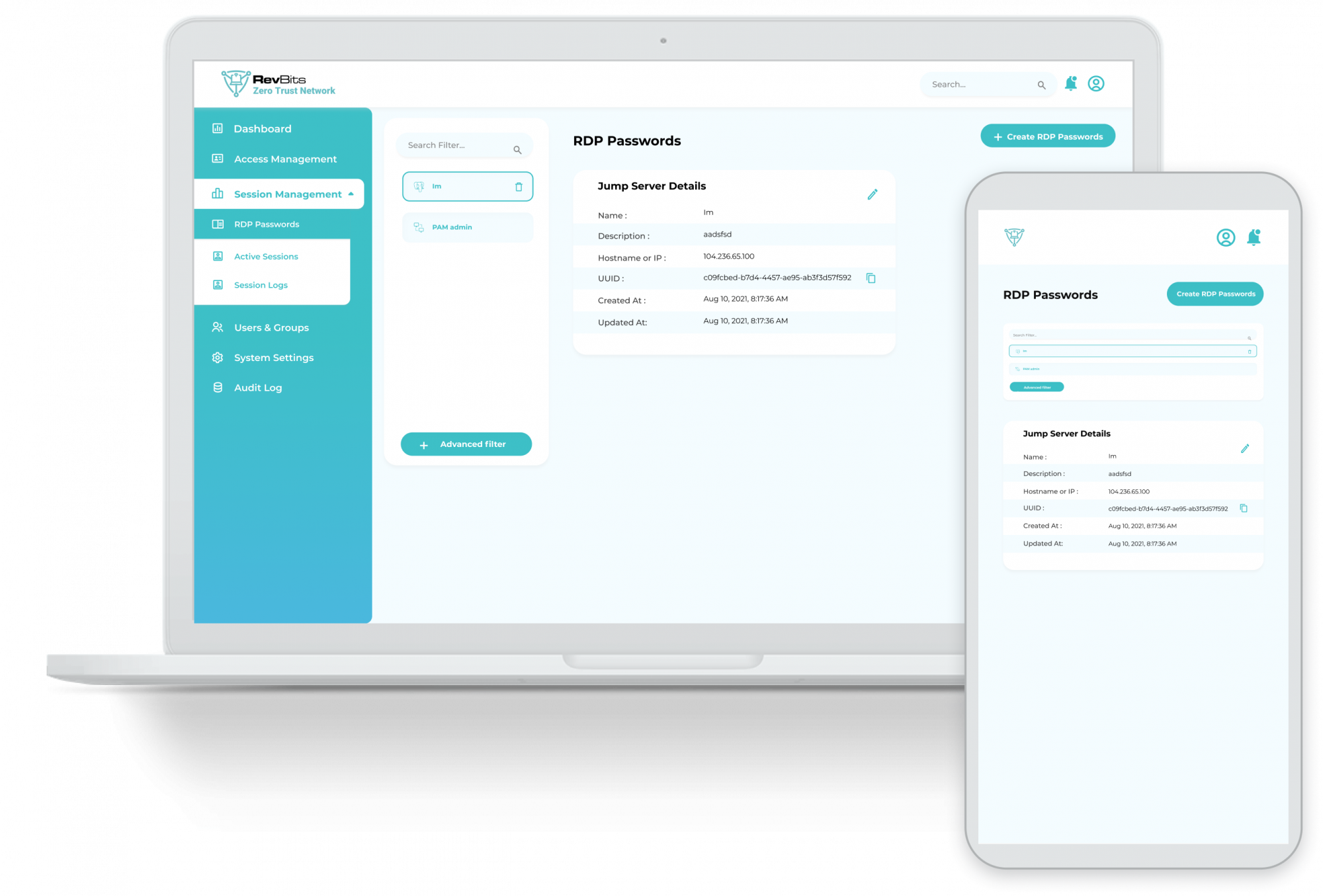
Full ZTN Session Management – Allows administrators to control all aspects of a remote access session, including monitoring, reviewing, recording and deleting any session with a single click, if necessary.
Load Balancing and High Availability – Regardless of the number of users, Rev Bits ZTN will automatically scale to meet access needs. RevBits dynamically allocates resources to support application scalability through auto-scaling and elastic load balancing capabilities. Additionally, RevBits ZTN's high availability architecture means it is always ready and available to ensure remote network access.
Choice of Authentication - RevBits ZTN authentication options include fingerprint, facial recognition, YubiKey, SAML, MFA app, text and many others. Extensive authentication options extend deeper perimeter security control.
Internal Asset Access Controls – RevBits ZTN allows for granular control, including access time and duration, and ensures that only the right host and the right assets are accessed. Fine-grained access control is the real power behind Revits ZTN.
Authentication
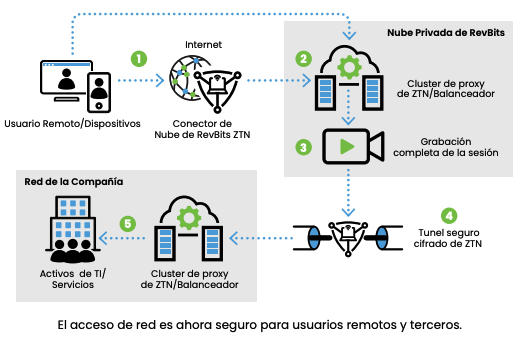
Authentication to RevBits ZTN in SaaS.
Remote access to the internal network through RevBits ZTN Proxy.
The session is recorded on RevBits ZTN.
All traffic is encrypted and secure through RevBits ZTN.
IT assets and applications are accessed remotely without installing any clients.
Components
A Powerful Platform – By combining RevBits ZTN with the RevBits Cyber Intelligence Platform, administrators get an unparalleled view of all sessions. Conducting a forensic investigation and putting together a timeline has never been so easy, intuitive and fluid.
Mobile Device Support – Full access and authentication support for all mobile platforms. The RevBits ZTN application is compatible with all types of current mobile devices.
Efficient User Access – Avoiding customer installations allows for seamless onboarding and quick access to all the assets a user needs on the internal network, with just a few clicks.